In this article, we explore the process of publishing Terraform modules on the Terraform Registry, facilitating module sharing and reuse in infrastructure as code projects.
Table of Contents
What is Terraform?
- It is an open-source IaaC (Infrastructure as a code) software tool where you define and create resources using providers in the declarative configuration language example JSON.
- With Terraform, You can package and reuse the code in the form of modules.
- It supports a number of cloud infrastructure providers such as AWS, Azure, GCP, IBM Cloud, OCI, etc.
What is Terraform Modules?
A Terraform module is a set of configuration code files with structured folder architecture. we create these modules to combine resources that are used for a specific single operation, which reduces the lines of code needed to create related infrastructure components.
What is Terraform Registry?
The Terraform Registry is a centralized repository for discovering, sharing, and distributing Terraform modules. Terraform is an open-source infrastructure as code (IaC) tool that allows users to define and provision infrastructure using a declarative configuration language. Terraform modules are reusable components that encapsulate infrastructure configurations and can be shared across different projects.
Key Features Of Terraform Registry
- Module Hosting: The registry hosts Terraform modules, which are pre-built configurations for specific infrastructure components or services. Modules can range from simple resources to complex multi-tier applications.
- Discoverability: Users can search and discover existing modules in the registry based on their specific infrastructure needs. This makes it easy to find and reuse configurations created by the community.
- Versioning: Modules in the Terraform Registry are versioned, allowing users to specify a particular version when including a module in their configuration. This ensures that infrastructure deployments are predictable and reproducible.
- Documentation: Each module in the registry typically includes documentation that explains how to use the module, its input variables, and any specific requirements or considerations.
- Collaboration: The registry facilitates collaboration by providing a centralized platform for sharing and improving Terraform configurations. Users can contribute to existing modules or publish their own modules for others to use.
- Provider Integration: The registry is integrated with Terraform providers, allowing users to easily reference modules and providers directly from their Terraform configurations.
What does Terraform Registry contains?
The Terraform Registry contains providers and modules:
- Providers:
- Official: Developed and maintained by HashiCorp (e.g., AWS, Azure, GCP).
- Partner: Developed and maintained by other organizations, actively supported by HashiCorp.
- Community: Developed and contributed by individual contributors.
- Modules:
- Reuse Principle (DRY): Modules promote the reuse of Terraform configurations.
- Registry Repository: Acts as a repository for reusable modules.
- Declaration Example:
module "vpc" { source = "terraform-aws-modules/vpc/aws" version = "3.19.0" }- Documentation: Provides detailed information on module usage, parameters, and configuration.
3. Organization Standardization:
- Standardizing Infrastructure: Organizations can standardize infrastructure provisioning using approved modules.
- Security Controls: Approved modules may include security controls to ensure a secure provisioning process.
Publish Modules Types
Public Terraform Modules
Modules are published on to github. It have to be named with a specific name pattern as well.
ex:- lets say you are creating a modules for AWS VPC then module have to be named terraform-aws-vpc. You publish you module to terraform registry via GitHub account.
- Supports versioning
- Generate document
- version history
- Show example
- available readme.md
Private Terraform modules
Private Terraform modules provide a way to encapsulate and share infrastructure configurations within an organization without making them publicly available on the Terraform Registry. Here are some key aspects of private modules:
- Visibility:
- Limited Access: Private modules are visible only to authorized users within the organization.
- Hosting:
- Self-Hosting: Private modules are hosted on a version control system, such as GitHub or GitLab, accessible only to approved team members.
- Access Control:
- Repository Access: Access to the version control repository is restricted, ensuring that only authorized users can view and modify the private module.
- Usage:
- In Corporate Environments: Private modules are often used in corporate environments where infrastructure configurations need to be shared among different projects but kept confidential.
- Security:
- Sensitive Configurations: Private modules are suitable for configurations containing sensitive information that should not be exposed publicly.
- Integration:
- Terraform Enterprise: Organizations using Terraform Enterprise can host and manage private modules within their Terraform Enterprise instance.
- Authentication:
- Authentication Mechanisms: Access to private modules may require authentication mechanisms to ensure that only authorized users can retrieve or modify the configurations.
- Documentation:
- Internal Documentation: While private modules may not have publicly accessible documentation, they often include internal documentation for team members.
- Collaboration:
- Team Collaboration: Private modules facilitate collaboration within a team or organization by allowing members to reuse and contribute to shared infrastructure configurations.
To use private modules, users typically reference them in their Terraform configurations using the appropriate version control system URL and credentials for accessing the private repository.
Verified Modules
Verified modules are reviewed by HashiCorp and actively maintained by contributors to stay up-to-date and compatible with both Terraform and their respective providers.
The verified badge appears next to modules that are published by a verified source.
Requirements for Publishing Modules

Standard Module Structure
Lets get an idea of the structure
Structure example:-
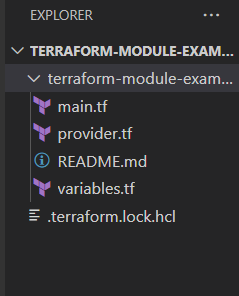
- main.tf – This must exists on the root directory. In other words this file is the entry point for your module.
- variables.tf , Outputs.tf– All variables and outputs should have one or two sentence descriptions that explain their purpose. (Variables that can be passed, outputs are output values)
- readme.md – description in a readme file.
- provider.tf-The provider.tf file in Terraform is a configuration file that specifies the cloud provider and its corresponding plugin that Terraform will use to manage resources in that provider.
Steps to Publish to Terraform Registry
Step1: Create your Terraform module configuration.
- main.tf – This must exists on the root directory. In other words this file is the entry point for your module.

- variables.tf , Outputs.tf– All variables and outputs should have one or two sentence descriptions that explain their purpose. (Variables that can be passed, outputs are output values)

- readme.md – description in a readme file.
- provider.tf-The provider.tf file in Terraform is a configuration file that specifies the cloud provider and its corresponding plugin that Terraform will use to manage resources in that provider.

Step2: Create a GitHub repository for your module
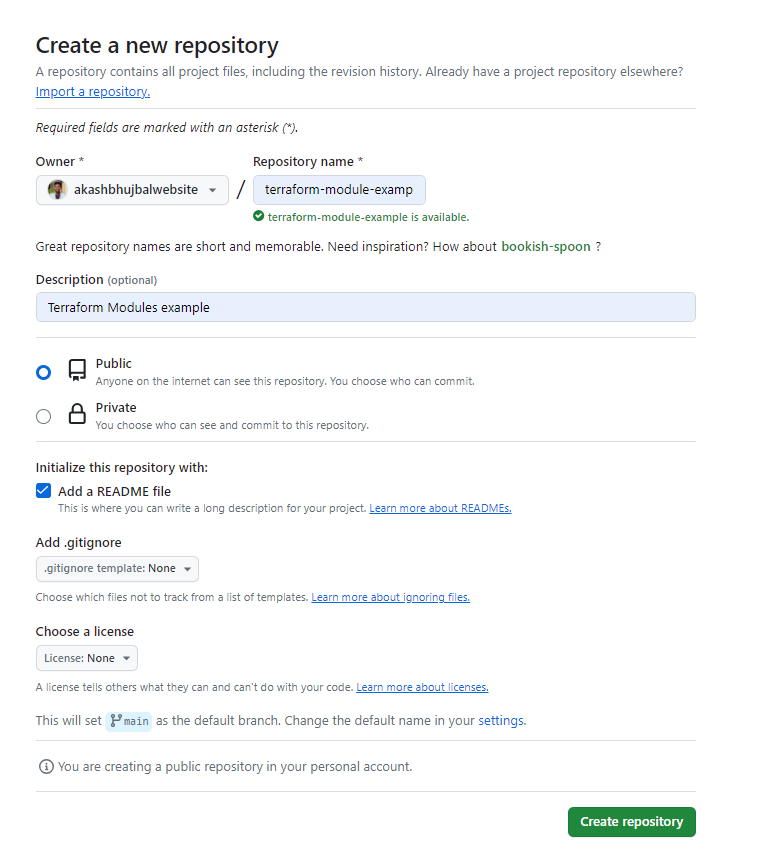
Step3: Push the content of your module configuration to the created repository.
- Clone the Git repo using Gitbash

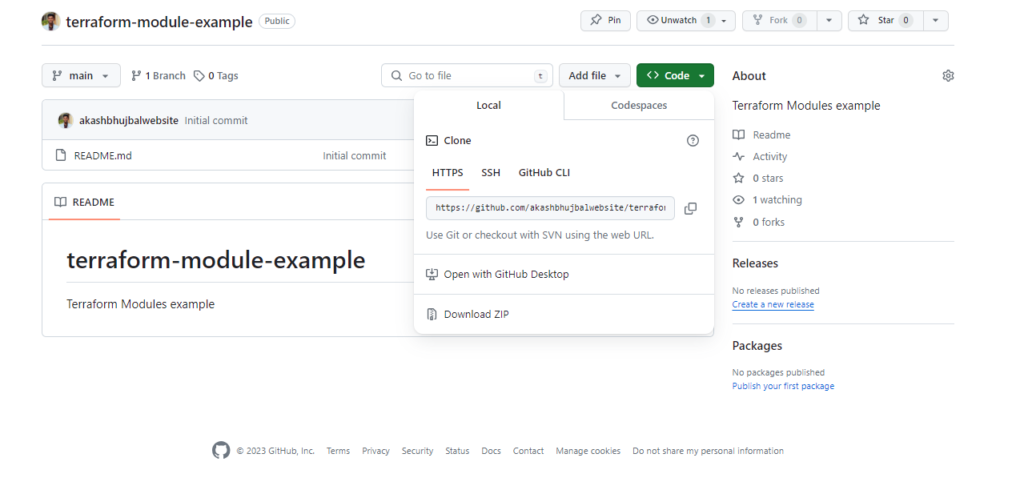
git clone https://github.com/akashbhujbalwebsite/terraform-module-example.git
mv main.tf terraform-module-example
mv provider.tf terraform-module-example/
mv variables..tf terraform-module-example/
cd terraform-module-example/

- Commit the Changes
git add .
git commit -m "adding terraform files"
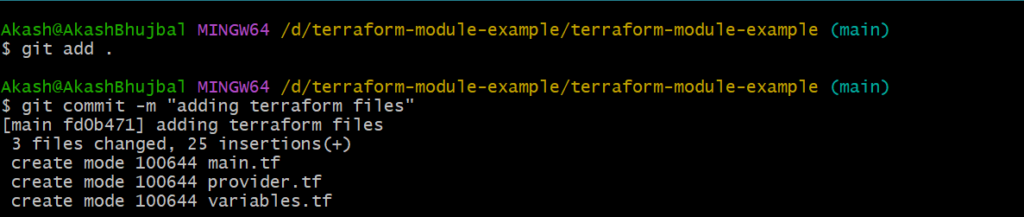
- Push the Content
git push origin main

Step4: Create a tag for your repository.
git tag -a v5.5.0 -m "Release version 5.5.0"
git push origin v5.5.0
git commit -m "Tag version 5.5.0"


Step5: Go to the Terraform registry and sign in with GitHub.


Step6: Click on publish and select module.

Step7: Select that GitHub repository.

Step8: Success, your module has been published!
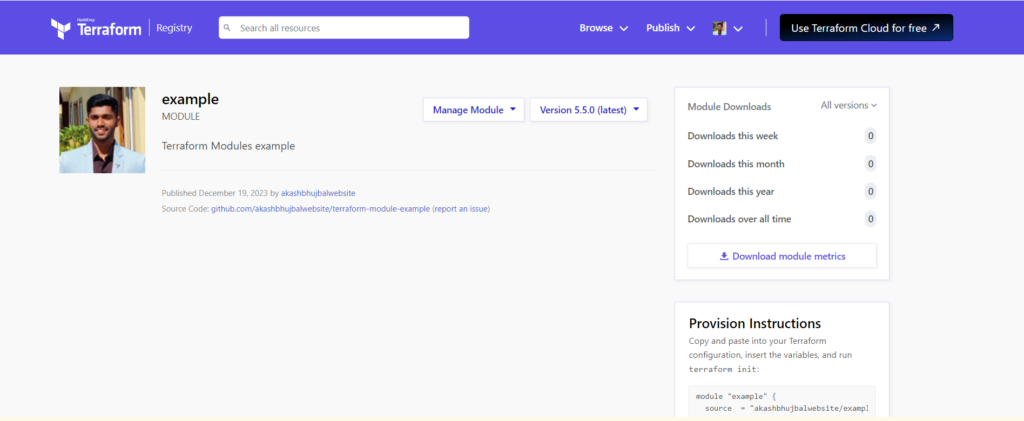
Conclusion:
Publishing modules to the Terraform Registry involves creating a well-documented module, versioning with Git tags, and using Terraform commands for authentication and publishing. This process empowers users to share, reuse, and contribute to modular infrastructure configurations seamlessly.
Reference:-
For reference visit the official website TerraformRegistry.
Any queries pls contact us @Devopshint.
Related Articles:
Terraform State File Management | Terraform Local State File | Terraform Remote State

